Movies, television series and web series have become very popular over the years. They have proved to be an important source of entertainment due to which, their demand has been increasing rapidly. Different PC games too, are preferred nowadays in order to entertain ones own self. While some people buy these products online or in brick and mortar shops, some download it from the internet. Torrentz has proven to be quite handy or useful in the downloading of these games and video files. The torrent files are easily available for free on the internet.
Advantages of using Torrentz:
Downloading torrent files from the internet has certain advantages over buying the product. This is why it is preferred. Some of the major advantages are as follows:
- Torrent follows a peer to peer protocol. There is no central network or no central main computer that controls all the transactions.
- Due to the peer to peer protocol, different paths are available to download the particular torrent file. If one path does not function properly, another path can be used in order to download the same file.
- While downloading a torrent file using an appropriate app, the download process can be paused, stopped or resumed at any time. Thus, if the computer goes off suddenly or abruptly, the user need not worry as the download can be resumed once the computer comes back on. The download progress is not lost.
- The torrent files are available free of cost on the internet. Hence it saves out on a lot of money.
- Different files are easy to find and download. Games, movies, songs and various other files are available.
- Certain software and operating systems are also available in the form of torrent files.
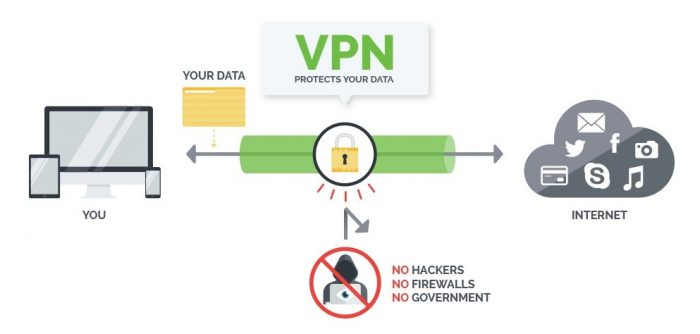
Many experts prefer and suggest the use of a VPN while downloading torrent files. VPN or virtual private network reroutes the files and other transactions with the help of a private network. This is done mainly for protection or for the purpose of the downloader’s safety. The data or the files downloaded in this case are encrypted while the IP address of the computer used for downloading the files is hidden. As such, nobody is able to track the activities of the user and all the operations are carried out anonymously.
What are the different types of VPN available?
There are different types of Virtual private networks available which can be classified based on the following aspects:
- The tunnelling procedure used. While downloading files using a VPN, the files are tunnelled and rerouted. Based on this tunnel protocol used, the VPN used can be classified into different types.
- Virtual private network can be classified based on the network provider edge. Edge devices are those which provide an entry into the networks
- The virtual private network can be classified based on the different levels of security provided. A network with greater levels of security is always preferred. This simply means extra protection.
- Many connections may be provided a similar virtual private network. Based on the number of connections provided with the similar network, the VPN can also be classified.
- The topology of connection used also serves as an important aspect for the classification of the different virtual private networks. Site to site and network to network topologies are very popular in today’s world.
A VPN for torrenting 2018 list is available on the internet which can be referred to before using any VPN for downloading torrent files. Using a VPN may slow down the internet speed if the company that provides the VPN is not a very efficient one. This is why, the best company ought to be chosen in order to prevention delay and time wastage. Some of the important aspects considered before formulating the best VPN for torrenting 2018 list are:
- Confidentiality – the VPN provider ought to maintain confidentiality as the main purpose of the VPN is to carry out processes anonymously.
- The sender must be authenticated. The number of cyber crimes taking place nowadays is quite high. Several spam reports have also been recorded. As such, it is important that the parties involved in the process are authentic.
- Data integrity should be maintained by the provider. The consistency and accuracy of the data should be maintained.
Authentication of the location is an important task that must be carried out by the VPN provider before the tunnel for the download process is established. For the authentication, passwords, pins, OTPs or biometrics can be used. Only after the termination point is authenticated should the download process begin. This ensures that the file downloaded reaches the right location and not in the hands of notorious cyber criminals. Many a times, the data may be classified and hidden with the help of encryption. Encryption is defined as the process of encoding a particular message or data file, which cannot be deciphered by a third party easily. A particular pattern is followed which is quite difficult to crack. Only the parties involved know about the pattern used. Once the message or information is delivered to the concerned destination, decryption is done when the reverse algorithm is used to obtain back the original message. Special encryption and decryption software is also available.
In certain cases, an unencrypted tunnel may also be provided by the virtual private network. However, this is the least preferred due to lack of adequate security. Certain overlay networks are also available. Overlay networks are like bunk beds or double decker buses. One network is built over another network. The two networks remain attached or connected to another at so called nodes. Initially, internet broadband was widely used. In this case, the internet was an overlay network built upon the telephone network. However, with the concept of internet calls flourishing, the telephone network is slowly turning into an overlay network that is built on the internet network.
With the help of a virtual private network, several applications not available in a particular region can be made available. Such networks have the potential to make all the applications found on the internet available to the whole world. The occurrence of cyber crimes like phishing and hacking is least likely when a VPN is used. Virtual private networks are highly helpful and it is hoped that maximum users will employ a VPN for torrenting 2018 onwards.
